No business wants to suffer a data breach. But unfortunately, in today’s environment, it’s difficult to completely avoid them. Approximately 83% of organizations have experienced more than one data breach according to IBM Security in 2022.
These breaches can hurt businesses in numerous ways. First, there is the immediate cost of remediating the breach. Then, there are the lost productivity costs to consider. Now add lost business on top of that, and lost customer trust. A business could also have extensive legal costs associated with a breach as well, making it a true black swan event.
According to IBM Security’s report, the cost of a data breach climbed once again in 2022. The global cost of one breach is now $4.4 million, up 2.6% from last year. If your business is in the U.S., the cost rises to $9.4 million, while in Canada, the average data breach “only” costs companies around $5.6 million.
Costs for smaller companies tend to be a little lower, but breaches are often more devastating to SMBs. They don’t have the same resources that larger companies do to offset all those costs and remediate the situation.
It’s estimated that 60% of small companies go out of business within six months of a cybersecurity breach
Companies don’t need to resign themselves to the impending doom of a data breach. There are some proven tactics they can use to mitigate the costs. These cybersecurity practices can limit the extent of the damage a cyberattack can cause, and help mitigate it better.
All these findings come from the IBM Security report. They include hard facts on the benefits of bolstering your cybersecurity strategy.
Cybersecurity Tactics For Reducing the Impact of a Breach
Use a Hybrid Cloud Approach
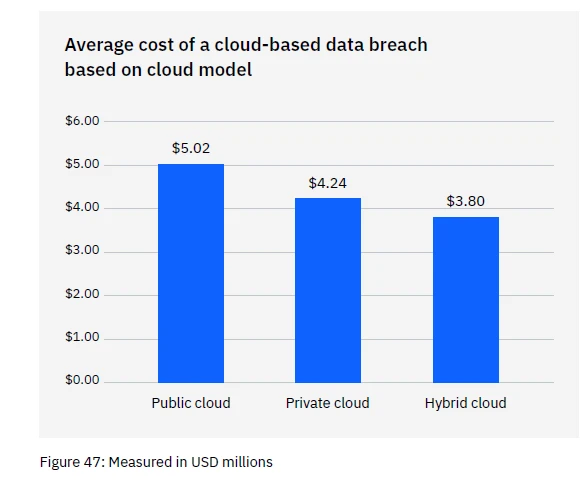
Most organizations use the cloud for data storage and business processes. Researchers found that 45% of all data breaches happen in the cloud, but all cloud strategies are not created equally.
Breaches in the public cloud cost significantly more than those in a hybrid cloud. Backing up for a second, what is a hybrid cloud? It is a combo solution where some data and processes are in a public cloud, and some are in a private cloud environment.
What some may find surprising is that using a hybrid cloud approach was also better than a private cloud.
Create an Incident Response Plan & Use It
You don’t need to be a large enterprise to create an incident response (IR) plan. The IR plan is a simple set of instructions and procedures for employees to follow, should any number of cybersecurity incidents occur.
In the case of ransomware for example, the first step should be disconnecting the infected device. IR plans improve the speed and effectiveness of a response in the face of a security crisis.
Having a practiced incident response plan reduces the costs and severity of a data breach. It lowers it by an average of $2.66 million per incident, according to the research.
Adopt a Zero-Trust Security Approach
While it is normally bad to be distrustful, in this case it is actually the correct call. Zero-trust is a collection of security protocols that work together to fortify a network. A few examples of these are:
Approximately 79% of critical infrastructure organizations haven’t adopted zero-trust approaches yet, even though implementing it can significantly reduce data breach costs. Organizations that don’t deploy zero trust tactics pay over $1 million more per data breach on average.
Use Security AI & Automation Tools
Using the right stack of security tools can make a big difference in the likelihood, impact, and costs incurred resulting from a data breach. Using tools that deploy security AI and automation bring the biggest cost savings, though they can be quite daunting for even the tech-savvy.
Data breach expense were reduced by a whopping 65.2% thanks to security AI and automation solutions, making this one of the best solutions for protecting against breaches. These types of solutions include tools like advanced threat protection (ATP), and can also include applications that hunt out threats and automatically handle the response.
How to Get Started on Improving Your Cyber Resilience
Many of these ways to lower data breach costs are simply best practices. You can get started by taking them one at a time and rolling out upgrades to your cybersecurity strategy, or find a trusted technology partner to help.
Working with a trusted IT provider, they will put together a roadmap on how to make your business resilient to cybersecurity threats. They will address the “low-hanging fruit” first, and then move on to longer-term projects.
One example of “low-hanging fruit” would be putting multi-factor authentication (MFA) in place. It’s low-cost and easy to put in place, and significantly reduces the risk of a cloud breach.
A longer-term project might be creating an incident response plan, or implementing a Security Operations Center (SOC). Then, you would set up a schedule to have your team drill on the plan regularly. During those drills, you could work out any kinks.
Need Help Improving Your Security & Reducing Risk?
Working with a trusted IT partner takes a lot of the security burden off your shoulders, especially with how overwhelming cybersecurity in particular is. Give us a call today to schedule a chat about building your cybersecurity roadmap!


